DevSecOps: Security in Modern DevOps
Integrate security practices seamlessly into your DevOps pipeline for secure software delivery.
Introduction
Understanding the DevSecOps Philosophy
DevSecOps represents a cultural shift where security becomes everyone's responsibility, not just the security team's. It emphasizes automation, collaboration, and continuous security throughout the software development lifecycle.
Industry Reality
Organizations implementing DevSecOps practices reduce security vulnerabilities in production by 60% and decrease mean time to remediation by 75%.
Core Principles of DevSecOps
- Shift Left Security: Integrate security early in development
- Automation First: Automate security testing and compliance
- Continuous Monitoring: Real-time security visibility
- Shared Responsibility: Security as everyone's concern
- Risk-Based Approach: Focus on high-impact vulnerabilities
Security Testing Types and Tools
Comprehensive security testing requires multiple approaches at different stages of the development lifecycle, from static code analysis to runtime protection.
| Testing Type | Stage | Tools | Purpose |
|---|---|---|---|
| SAST | Code | SonarQube, Checkmarx | Static code analysis |
| DAST | Runtime | OWASP ZAP, Burp Suite | Dynamic vulnerability testing |
| SCA | Dependencies | Snyk, WhiteSource | Dependency vulnerability scanning |
| IAST | Testing | Contrast Security, Veracode | Interactive application testing |
| Container Security | Build | Twistlock, Aqua | Container image scanning |
Implementing Static Application Security Testing
SAST tools analyze source code to identify security vulnerabilities without executing the program, making them ideal for early-stage security validation.
name: Security Scan
on:
push:
branches: [ main, develop ]
pull_request:
branches: [ main ]
jobs:
security-scan:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v3
- name: Run SonarCloud Scan
uses: SonarSource/sonarcloud-github-action@master
env:
GITHUB_TOKEN: ${{ secrets.GITHUB_TOKEN }}
SONAR_TOKEN: ${{ secrets.SONAR_TOKEN }}
- name: Run Semgrep
run: |
pip install semgrep
semgrep --config=auto --error .
- name: Upload SARIF results
uses: github/codeql-action/upload-sarif@v2
with:
sarif_file: semgrep.sarifContainer and Infrastructure Security
Container security extends beyond image scanning to include runtime protection, network policies, and secure configuration management across the entire container lifecycle.
- Scan base images for known vulnerabilities
- Implement multi-stage builds for minimal attack surface
- Use non-root users in container configurations
- Apply security policies with admission controllers
- Monitor runtime behavior for anomalies
# Multi-stage build for security
FROM node:18-alpine AS builder
WORKDIR /app
COPY package*.json ./
RUN npm ci --only=production
# Production stage
FROM node:18-alpine AS production
# Create non-root user
RUN addgroup -g 1001 -S nodejs
RUN adduser -S nextjs -u 1001
# Set secure permissions
WORKDIR /app
COPY --from=builder --chown=nextjs:nodejs /app/node_modules ./node_modules
COPY --chown=nextjs:nodejs . .
# Switch to non-root user
USER nextjs
# Remove unnecessary packages
RUN apk del --purge wget curl
EXPOSE 3000
CMD ["npm", "start"]Security Alert
Running containers as root increases the blast radius of potential security breaches. Always use non-privileged users in production containers.
Kubernetes Security Best Practices
Kubernetes environments require specific security configurations including RBAC, network policies, pod security standards, and admission controllers to maintain a secure orchestration platform.
apiVersion: v1
kind: Pod
metadata:
name: secure-pod
spec:
securityContext:
runAsNonRoot: true
runAsUser: 1000
fsGroup: 2000
seccompProfile:
type: RuntimeDefault
containers:
- name: app
image: myapp:latest
securityContext:
allowPrivilegeEscalation: false
readOnlyRootFilesystem: true
capabilities:
drop:
- ALL
add:
- NET_BIND_SERVICE
resources:
limits:
memory: "128Mi"
cpu: "500m"
volumeMounts:
- name: tmp
mountPath: /tmp
volumes:
- name: tmp
emptyDir: {}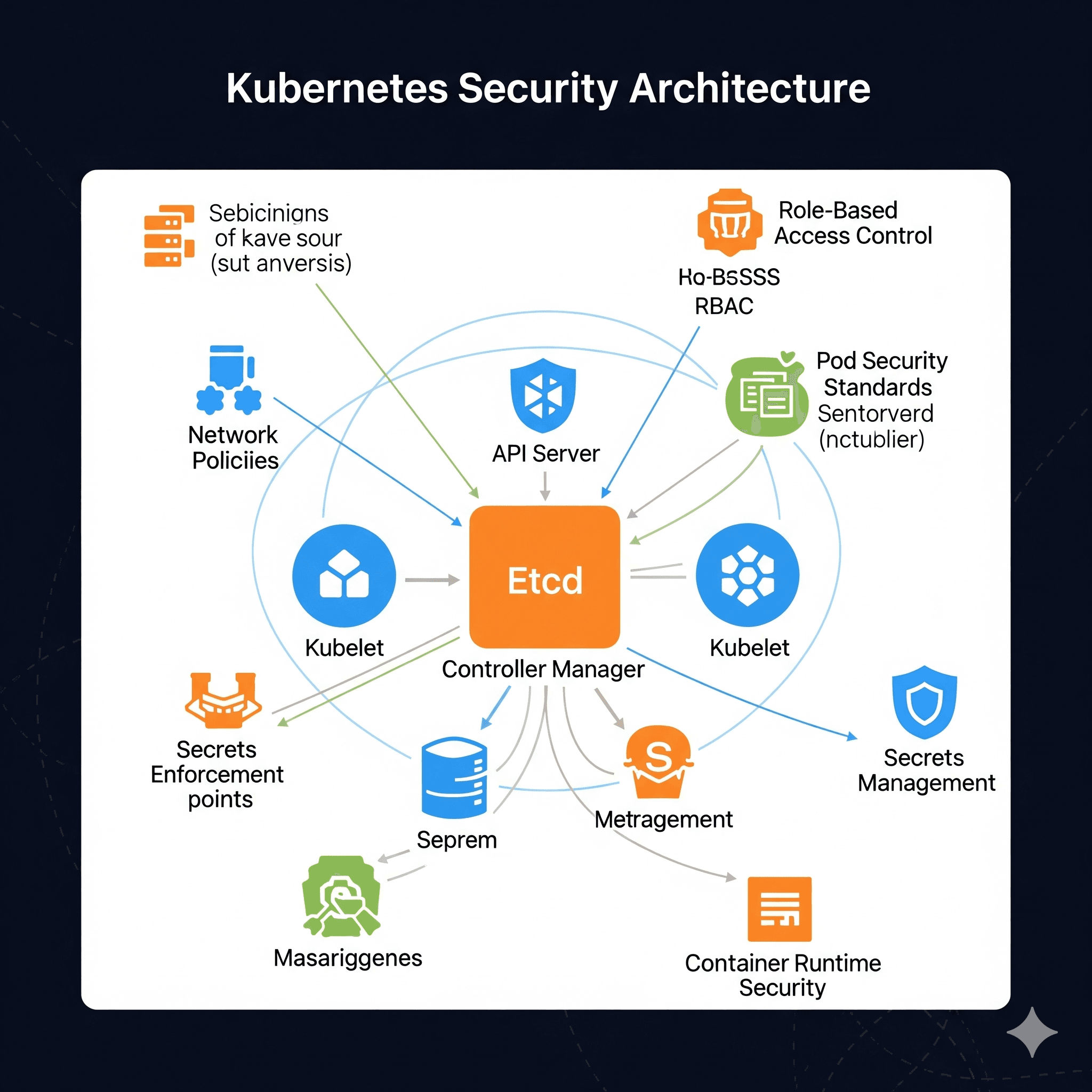
Secrets Management and Compliance
Proper secrets management is crucial for DevSecOps success, requiring secure storage, rotation, and access control for sensitive information like API keys, passwords, and certificates.
| Solution | Use Case | Features | Best For |
|---|---|---|---|
| HashiCorp Vault | Enterprise secrets | Dynamic secrets, encryption | Multi-cloud environments |
| AWS Secrets Manager | AWS workloads | Automatic rotation, integration | AWS-native applications |
| Azure Key Vault | Azure resources | HSM support, certificates | Microsoft ecosystem |
| Kubernetes Secrets | Container orchestration | Native integration | Kubernetes workloads |
#!/bin/bash
# Vault secrets integration script
# Authenticate with Vault
vault auth -method=aws
# Retrieve database credentials
DB_CREDS=$(vault kv get -format=json secret/myapp/database)
DB_USER=$(echo $DB_CREDS | jq -r '.data.username')
DB_PASS=$(echo $DB_CREDS | jq -r '.data.password')
# Export as environment variables
export DATABASE_URL="postgresql://$DB_USER:$DB_PASS@db:5432/myapp"
# Start application with secrets
exec "$@"Compliance and Governance
DevSecOps must address regulatory requirements and organizational governance through policy automation, audit trails, and continuous compliance monitoring.
- Policy as Code: Define compliance rules programmatically
- Automated Auditing: Continuous compliance checking
- Immutable Infrastructure: Prevent configuration drift
- Audit Logging: Comprehensive activity tracking
- Access Controls: Principle of least privilege
Compliance Tip
Use Open Policy Agent (OPA) to implement policy as code, enabling consistent policy enforcement across your entire infrastructure stack.
Security Monitoring and Incident Response
Effective DevSecOps includes continuous monitoring, threat detection, and automated incident response capabilities to quickly identify and mitigate security issues in production environments.
groups:
- name: security-alerts
rules:
- alert: HighFailedLoginAttempts
expr: rate(failed_login_attempts_total[5m]) > 10
for: 2m
labels:
severity: warning
annotations:
summary: "High failed login attempts detected"
- alert: UnauthorizedAPIAccess
expr: rate(http_requests_total{status="401"}[1m]) > 5
for: 1m
labels:
severity: critical
annotations:
summary: "Potential brute force attack detected"
- alert: ContainerPrivilegeEscalation
expr: increase(container_privilege_escalation_total[5m]) > 0
for: 0s
labels:
severity: critical
annotations:
summary: "Container privilege escalation detected""Security is not a product, but a process. It's not a destination, but a journey. And it's most definitely not something you can bolt on at the end."
— Bruce Schneier, Security Technologist
Building Security Culture
Successful DevSecOps transformation requires cultural change, education, and making security practices accessible and integrated into daily development workflows.
- Provide security training for all team members
- Implement security champions programs
- Make security tools easy to use and integrate
- Create blameless security incident reviews
- Celebrate security improvements and fixes

Success Metric
Measure DevSecOps maturity by tracking security fix deployment times, vulnerability detection rates, and developer security knowledge assessments.
Conclusion
DevSecOps transforms security from a bottleneck into an enabler, allowing organizations to deliver secure software at speed. Success requires tooling, processes, and most importantly, a cultural shift toward shared security responsibility.
Reading Progress
0% completed
Article Insights
Share Article
Quick Actions
Stay Updated
Join 12k+ readers worldwide
Get the latest insights, tutorials, and industry news delivered straight to your inbox. No spam, just quality content.
Unsubscribe at any time. No spam, ever. 🚀
