Secure data in transit and at rest with advanced encryption technologies.
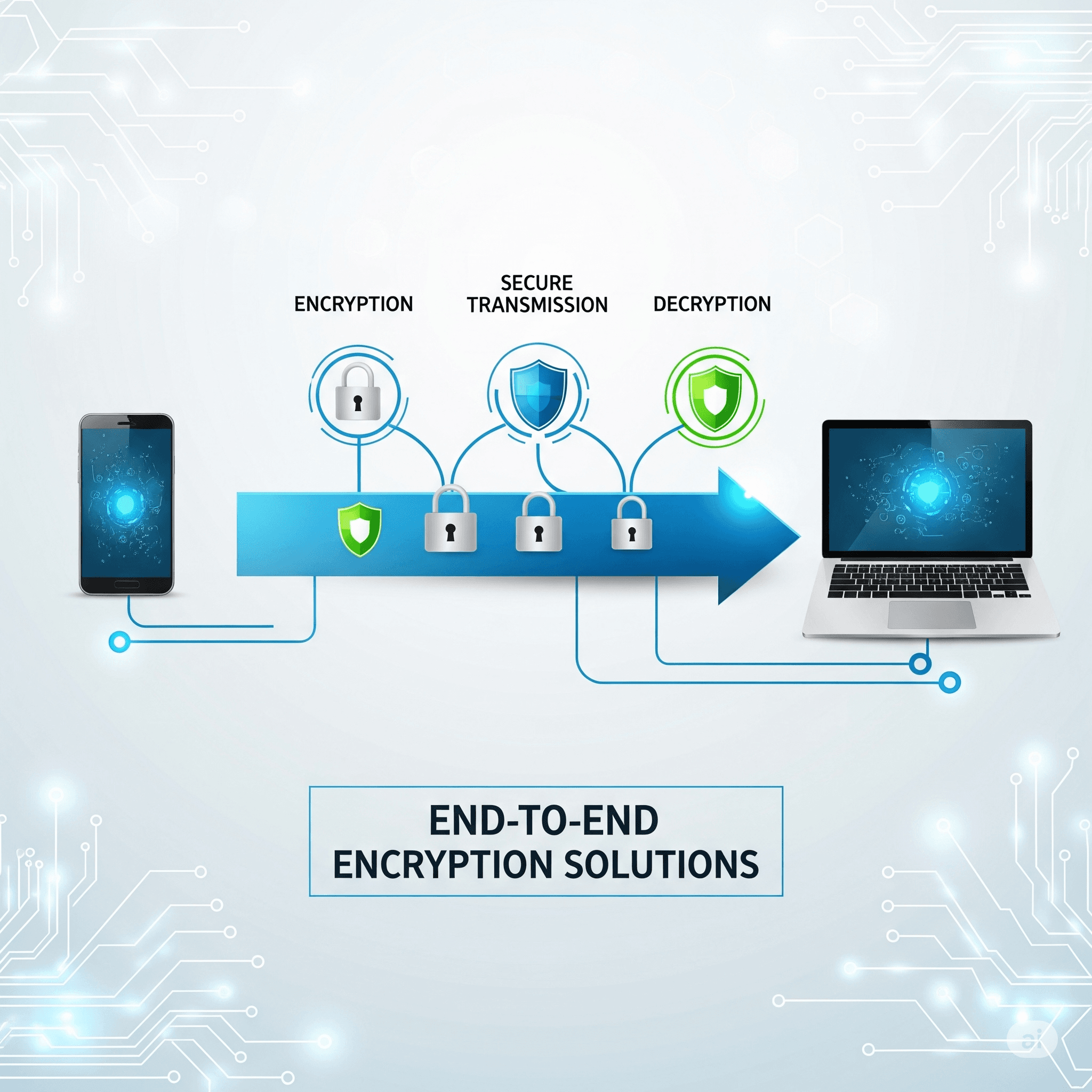
Our End-to-End Encryption Solutions provide comprehensive data protection using advanced cryptographic technologies to secure information from source to destination and throughout its lifecycle. We specialize in data-in-transit encryption, data-at-rest protection, key management systems, and regulatory compliance implementation. Our approach combines military-grade encryption standards, seamless integration capabilities, and user-friendly interfaces to deliver robust security solutions that protect sensitive data, ensure privacy, maintain data integrity, and meet regulatory requirements while preserving system performance and user experience.
Comprehensive encryption covering data in transit, at rest, and in use with military-grade AES-256 encryption standards.
Advanced cryptographic signing and integrity verification ensuring data authenticity and preventing unauthorized modifications.
Built-in compliance support for GDPR, HIPAA, PCI DSS, and industry-specific regulations with audit-ready encryption.
Easy integration with existing systems, applications, and workflows without disrupting business operations or user experience.
Discover how our comprehensive approach delivers measurable results for your business
State-of-the-art encryption technologies with multiple encryption standards, key generation, and cryptographic protocol implementation.
Robust key management infrastructure with secure key generation, distribution, storage, and lifecycle management capabilities.
End-to-end secure communication channels with data integrity verification, authentication, and non-repudiation capabilities.
We follow a systematic approach to ensure your project's success from start to finish
Comprehensive security assessment with data classification, threat analysis, and encryption requirements identification.
Encryption strategy development with architecture design, technology selection, and integration planning.
Encryption system implementation with key management infrastructure deployment and security controls configuration.
Comprehensive testing with encryption validation, performance assessment, and security verification procedures.
Production deployment with continuous monitoring, key management, and ongoing security maintenance.
We leverage cutting-edge technologies to deliver robust, scalable solutions
Get answers to common questions about our services
Let's discuss how we can help transform your business with our expert cybersecurity services solutions.