Detect and respond to cyber threats instantly with AI-powered monitoring and analytics.
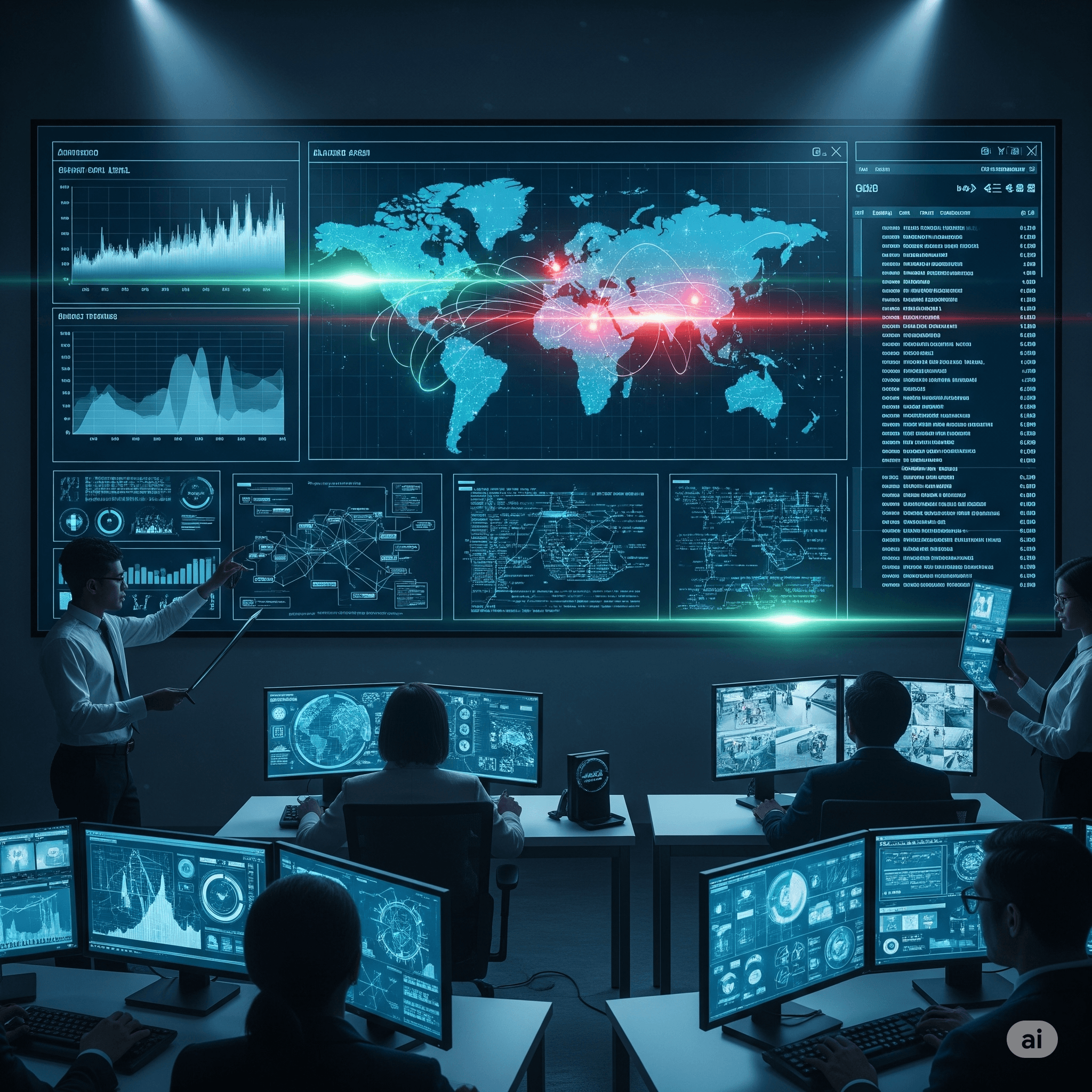
Our Real-Time Threat Monitoring platform provides comprehensive cybersecurity protection through advanced artificial intelligence, machine learning, and behavioral analytics that continuously monitor, detect, and respond to cyber threats in real-time. Built for organizations requiring robust security posture and rapid threat response, our solution combines 24/7 monitoring, automated threat detection, incident response orchestration, and predictive threat intelligence to protect critical assets, prevent data breaches, and ensure business continuity against evolving cyber threats.
Advanced machine learning algorithms that identify known and unknown threats with high accuracy while minimizing false positives through behavioral analysis.
Round-the-clock monitoring by expert security analysts with automated threat response and escalation procedures for immediate threat mitigation.
Intelligent response automation that contains threats, preserves evidence, and initiates recovery procedures to minimize business impact and downtime.
Proactive threat hunting and intelligence that anticipates emerging threats and vulnerabilities before they impact your organization.
Discover how our comprehensive approach delivers measurable results for your business
Intelligent threat detection platform that uses AI and machine learning to identify, analyze, and prioritize security threats across all network endpoints and systems.
Comprehensive security operations platform with 24/7 monitoring, expert analysis, and coordinated incident response capabilities.
Proactive threat hunting platform that identifies emerging threats, vulnerabilities, and attack patterns before they impact organizational security.
We follow a systematic approach to ensure your project's success from start to finish
Comprehensive security posture evaluation with asset discovery, vulnerability assessment, and threat landscape analysis to establish monitoring baseline.
Implementation of threat monitoring infrastructure with sensor deployment, SIEM configuration, and integration with existing security tools.
Training and customization of AI threat detection models based on organizational environment, threat patterns, and business context.
Integration with Security Operations Center capabilities and implementation of automated response procedures and escalation workflows.
Ongoing threat monitoring with continuous model refinement, threat intelligence updates, and security posture optimization.
We leverage cutting-edge technologies to deliver robust, scalable solutions
Get answers to common questions about our services
Let's discuss how we can help transform your business with our expert cybersecurity solutions.