Protect remote work environments with robust cybersecurity measures.
Our Secure Remote Work Infrastructure service provides comprehensive cybersecurity solutions that protect distributed workforces through advanced security technologies, zero-trust architectures, and comprehensive endpoint protection. We specialize in secure remote access, data protection, identity management, and threat detection for remote work environments. Our approach combines cybersecurity expertise, cloud security technologies, and remote work best practices to deliver robust security frameworks that ensure data integrity, prevent cyber threats, maintain regulatory compliance, and enable secure productivity while supporting flexible work arrangements and maintaining user experience.
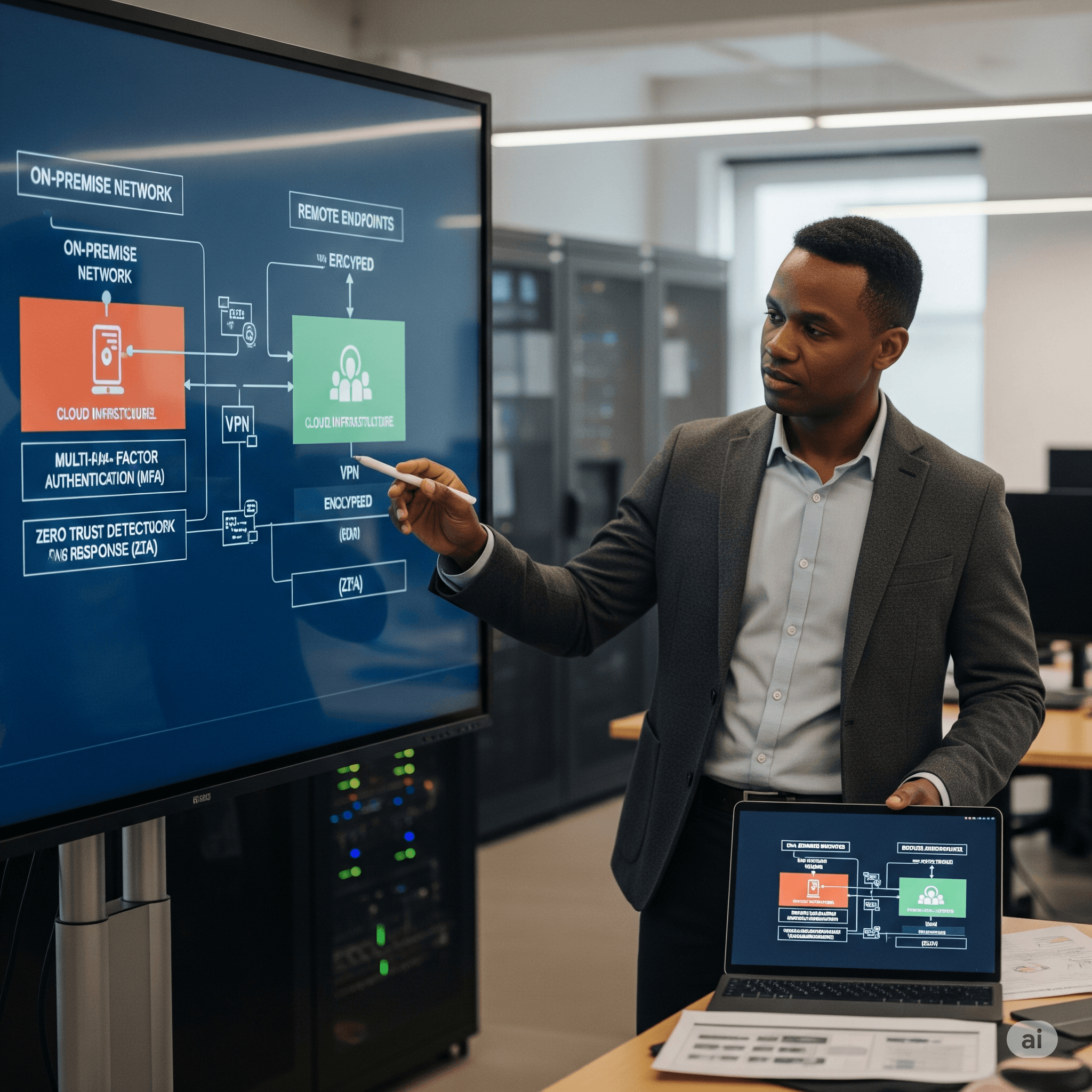
Comprehensive zero-trust framework with multi-factor authentication, continuous verification, and least-privilege access for complete remote work security.
Complete endpoint security with antivirus, encryption, device management, and threat detection protecting all remote work devices.
Enterprise-grade VPN, Virtual Desktop Infrastructure (VDI), and secure cloud access ensuring protected connectivity from anywhere.
Regulatory compliance support with GDPR, HIPAA, SOC 2 adherence, audit trails, and data governance for regulated industries.
Discover how our comprehensive approach delivers measurable results for your business
Advanced zero-trust security framework with comprehensive identity management, access controls, and continuous authentication.
Comprehensive endpoint protection with encryption, threat detection, and data loss prevention for all remote work devices.
Enterprise-grade remote access solutions with VPN, VDI, and secure cloud connectivity ensuring protected remote work.
We follow a systematic approach to ensure your project's success from start to finish
Comprehensive security assessment with remote work risk analysis, vulnerability identification, and compliance evaluation.
Zero-trust security architecture design with technology selection, policy development, and implementation planning.
Security infrastructure deployment with endpoint protection, VPN setup, and security tool configuration.
Security awareness training with policy implementation, best practices education, and compliance procedures.
24/7 security monitoring with threat detection, incident response, and continuous security optimization.
We leverage cutting-edge technologies to deliver robust, scalable solutions
Get answers to common questions about our services
Let's discuss how we can help transform your business with our expert future of work services solutions.